Deem Mobile Application Sign-In
To sign-in to the Deem Mobile Application, the Deem account email address and password is used.
This can be different from signing in to the Deem Application where the user signs in with a username and password or with sign-on credentials from another application called Single Sign On (SSO).
Finding your mobile sign-in email address
If you do not use the Deem account email address to sign-in to the Deem Application, you can find your Deem Mobile email address in the Deem Application.
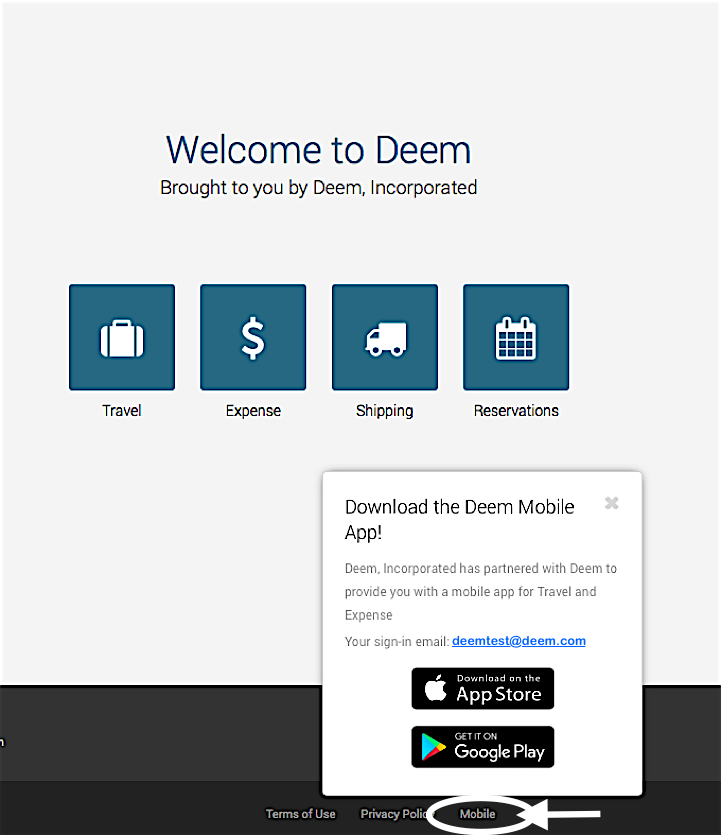
In the New UI, the mobile link is displayed in the Mobile Popup accessible from the footer of every page.
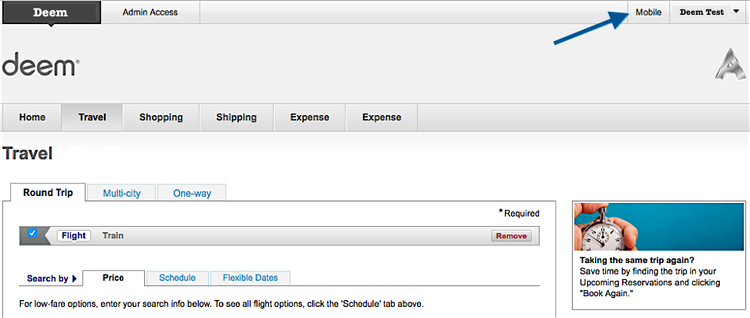
Or, if you are using the older version of our UI, it is displayed in the Mobile page accessible from the Mobile tab at the top of every page.
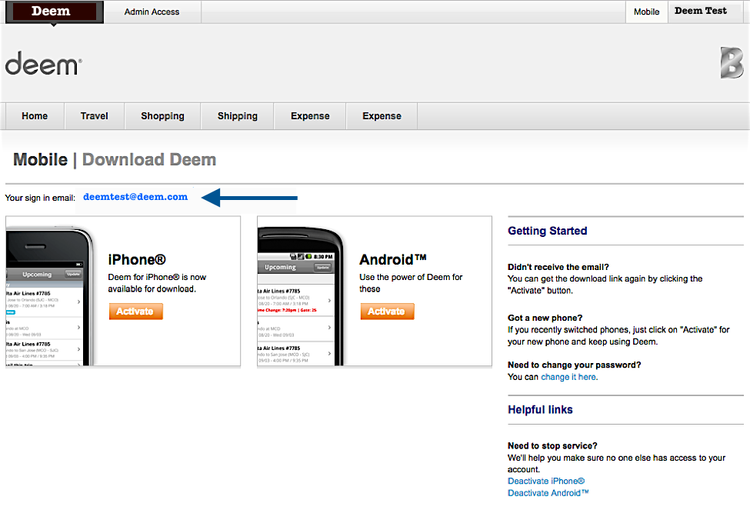
Click the Mobile tab and your sign in email will display on the Mobile | Download Deem page.
Establishing your mobile sign-in password
If you do use a password to sign-in to the Deem Application, use this same password to sign-in to the Deem Mobile Application.
- Enter your email and password and tap the Sign In button.
If you use sign on credentials from another application commonly called Single Sign On (SSO) to sign-in to the Deem Application, you will need to establish a password to use to sign-in to the Deem Mobile Application.
The easiest way to establish a password is to use the Deem Mobile Application.
...
Below is the high-level diagram for the Mobile SSO User Experience flow.
Mobile SSO Qualifications
- Desktop SSO must be implemented.
- Please see: Implementing Single Sign-On (SSO) for Desktop for more information.
- Deem Mobile Application opens a secure and private In App Browser to initiate the SAML authentication flow.
- Both SP-Initiated and IdP-Initiated are supported.
- Mobile SSO uses the same Console Site SSO Configurations as Desktop SSO.
There are 2 Mobile specific settings, Enable Mobile SSO and Mobile Company SSO End Point, - The user account must exist and be active to login using Mobile SSO.
NOTE: Mobile SSO does not include profile provisioning like Desktop SSO. - If the site is configured for Hybrid SSO (both Username/Password and SSO authentication), then the Deem Mobile Application will only support SSO authentication.
Only users who have access to the customer's SSO Service will be able to sign in to the Deem Mobile Application.
Configuring Mobile SSO
Shared Desktop and Mobile Configuration
To configure Desktop and Mobile SSO together, two applications in your SSO Service will need to be configured, one for Desktop and one for Mobile.
The Mobile application will be configured with a Virtual Server Id so the SAML assertion will be processed for mobile.
The Virtual Server Id can be a string or URL but must be a different URL than the Desktop Application SAML Audience.
The following information is needed to configure your SSO Service.
- Desktop Application SAML Endpoint: https://go.deem.com/sp/ACS.saml2
- Desktop Application SAML Audience: https://go.deem.com
- Mobile Application SAML Endpoint: https://go.deem.com/sp/<Base64 Encoded Element of PingFederate Virtual Server Id>/ACS.saml2
The element decoded is of the form {“vsid”:“<virtual-server-id>”} - Mobile Application SAML Audience: <PingFederate Virtual Server Id>
- Relay State: If configuring for IdP-Initiated and multiple sites, a unique URL for your Deem domains that should be included with the SAML assertions. Your Deem Integrations Manager will provide these URLs.
The following information is required for Deem to complete the configuration.
- Issuer: The same unique identifier for Desktop SSO that represents you as a customer in the SAML assertion. Typically, this is a string or a URL.
- The X509 Certificate that is used to digitally sign your SAML assertions. This will be used by Deem to validate the SAML assertions you send.
- Mobile Company SSO Endpoint URL: If configuring for IdP-Initiated, this is the URL that the Deem Mobile Application will open to initiate the SAML authentication flow.
Separate Mobile Configuration
To configure Mobile SSO separately from Desktop SSO is simpler.
The following information is needed to configure your SSO Service.
Note: This information is the same for Desktop SSO. (please see Implementing Single Sign-On (SSO) for Desktop for more information)
- Deem SAML Endpoint: https://go.deem.com/sp/ACS.saml2
- SAML Audience: https://go.deem.com
- Relay State: If configuring for IdP-Initiated and multiple sites, a unique URL for your Deem domains that should be included with the SAML assertions. Your Deem Integrations Manager will provide these URLs.
The following information is required for Deem to complete the configuration.
- Issuer: A unique identifier for mobile that represents you as a customer in the SAML assertion. Typically, this is a string or a URL.
- The X509 Certificate that is used to digitally sign your SAML assertions. This will be used by Deem to validate the SAML assertions you send.
- Mobile Company SSO Endpoint URL: If configuring for IdP-Initiated, this is the URL that the Deem Mobile Application will open to initiate the SAML authentication flow.
Sample Mobile SAML Response and Assertion
| <samlp:Response ID="uuid-50DEF5D7-9692-867A-F298-BB580563C366" IssueInstant="2019-09-13T17:29:58Z" Version="2.0" Destination="https://go.deem.com/sp/ACS.saml2" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"> <ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/> <ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/> <ds:Reference URI="#uuid-50DEF5D7-9692-867A-F298-BB580563C366"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/> <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/> <ds:DigestValue>ArFqYXonwiw5WjkeZZF7r7thNJM=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <ds:SignatureValue>fStXbwEmy1kyoXwTv80pl7zINGizj7ufIxiWSCdCFgpW3b1htQkZmTgMLWpii30U7DUTd3V+SNFIRB7QRB4kne27R8Gu5sxxLnA7bLx4uZzeTUHg+rZyEdz6bD/izxpgdR6tjnHyKLrTpe3qwUtGAFdTHCTJI40YWZXw2HMvjIYMHxGIaukuqE9RL6a4YwM3ag1kXMhvUQP5mUKjxNPj39R45u87pV0xnDdfcs2ibLNyK/1wqD5m272C4pL61dAHDEfTMzlVpqhRwSfbVw/fB+KGk0GG0oB2KfIzamIy8AabAADQYtYSyque/vFG+pD+lb36N1Z6PvWmmnFxmnCvgA==</ds:SignatureValue> </ds:Signature> <samlp:Status> <samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/> </samlp:Status> <saml:Assertion ID="uuid-75065D54-2F3A-FE93-0864-13EEDFC85A4F" IssueInstant="2019-09-13T17:29:58Z" Version="2.0" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"> <saml:Issuer>SsoMobile</saml:Issuer> <saml:Subject> <saml:NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:unspecified">ddeem@deem.com</saml:NameID> <saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <saml:SubjectConfirmationData Recipient="https://go.deem.com/sp/ACS.saml2" NotOnOrAfter="2019-09-13T17:39:58Z"/> </saml:SubjectConfirmation> </saml:Subject> <saml:Conditions NotBefore="2019-09-13T17:29:58Z" NotOnOrAfter="2019-09-13T17:39:58Z"> <saml:AudienceRestriction> <saml:Audience>https://go.deem.com</saml:Audience> </saml:AudienceRestriction> </saml:Conditions> <saml:AuthnStatement AuthnInstant="2019-09-13T17:29:58Z"> <saml:AuthnContext> <saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</saml:AuthnContextClassRef> </saml:AuthnContext> </saml:AuthnStatement> <saml:AttributeStatement> <saml:Attribute Name="siteUrlName"> <saml:AttributeValue>acme</saml:AttributeValue> </saml:Attribute> </saml:AttributeStatement> </saml:Assertion></samlp:Response> |